Cisco AnyConnect VPN
- Cisco Anyconnect Vpn Client Free Download For Mac Os X 10.8
- Cisco Anyconnect Vpn Client 10.8 Free
- Cisco Anyconnect Vpn Client 10.8 Login
- Cisco Anyconnect Vpn Client 10.8 Download
Secure VPN access for remote workers. Cisco AnyConnect Secure Mobility Client empowers remote workers with frictionless, highly secure access to the enterprise network from any device, at any time, in any location while protecting the organization. For organizations of all sizes that need to protect sensitive data at scale, Duo is the user. Stop the local user (vpn) from login to ADSM and CLI. Access Lists for VPN Client. Refer to the steps below on how to configure Cisco AnyConnect VPN with CLI. Setup TFTP Server on RHEL 8. Download Cisco AnyConnect 4.8 WebDeploy Client (anyconnect-win-4.8.02042-webdeploy-k9.pkg) from Cisco.com and upload to TFTP Server. Install the VPN client. Download the Cisco AnyConnect VPN for Windows installer. Double-click the InstallAnyConnect.exe file. When a message saying the Cisco AnyConnect client has been installed, click OK. Connect to the Stanford VPN. Launch the Cisco AnyConnect Secure Mobility Client client.
Authorized employees of the university can use Cisco AnyConnect to access restricted campus resources, such as Banner, when using an Adams State University computer from off campus.
To request VPN access please submit a ticket at https://helpdesk.adams.edu. Please note, VPN access may need approval from a supervisor, CIO, and/or HR where applicable. Computing Services technicians will assist with client installation and configuration.
Connect with the Cisco AnyConnect Client
You will need to authenticate using your ASU username and password as well as a certificate to connect using the Cisco AnyConnect Client. If you have not yet imported your certificate please see certificate import instructions below.
- Click Start > All Programs
- Click the Cisco Folder.
- Click the Cisco Anyconnect Secure Mobility Client program.
- You may also have an icon in your system tray for the Cisco Anyconnect client. You can also launch the client by double clicking the icon in the system tray.
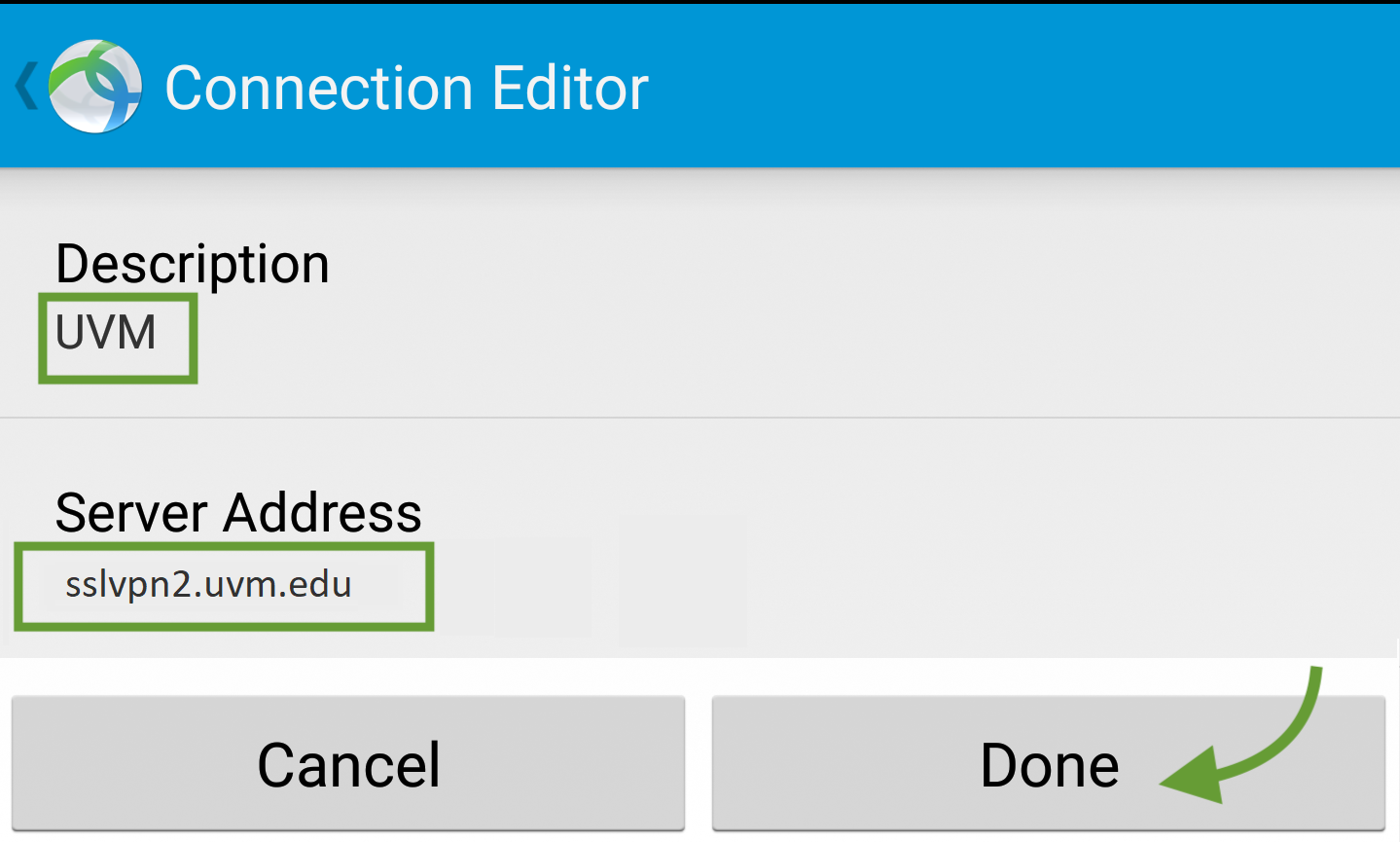
- Enter vpn1.adams.edu in the text box and click Connect
- You will be prompted to select your certificate. Select the certificate with the name cn=yourusername issuer of vpn1.adams.edu.
- Enter your ASU username and password
- The icon in the system tray will show a lock when connected to the vpn.
Disconnect from the Cisco Anyconnect VPN client
- Right Click the Cisco Anyconnect VPN client icon in your system tray
- Select Disconnect
Please be sure to disconnect from the VPN client when you no longer need access to restricted internal resources.
Import Certificate for Multifactor Authentication
- After you successfully enter your username and password the certificate will be downloaded to your computer. Right click on the certificate and select Install PFX
- The Certificate Import Wizard will start. Select Current User as the store location, then click next.
- Verify file location, then click next
- Enter the password for the certificate that you received in the email from Computing Services.
- Select the 'Place all certificates in the following store' option and click Browse. Select 'Personal' as the certificate store location.
- Click next, then Finish to complete the Certificate Import Wizard. You will see The import was successful on completion of certificate import.
Downloading AnyConnect VPN Client for Windows / MAC / Linux
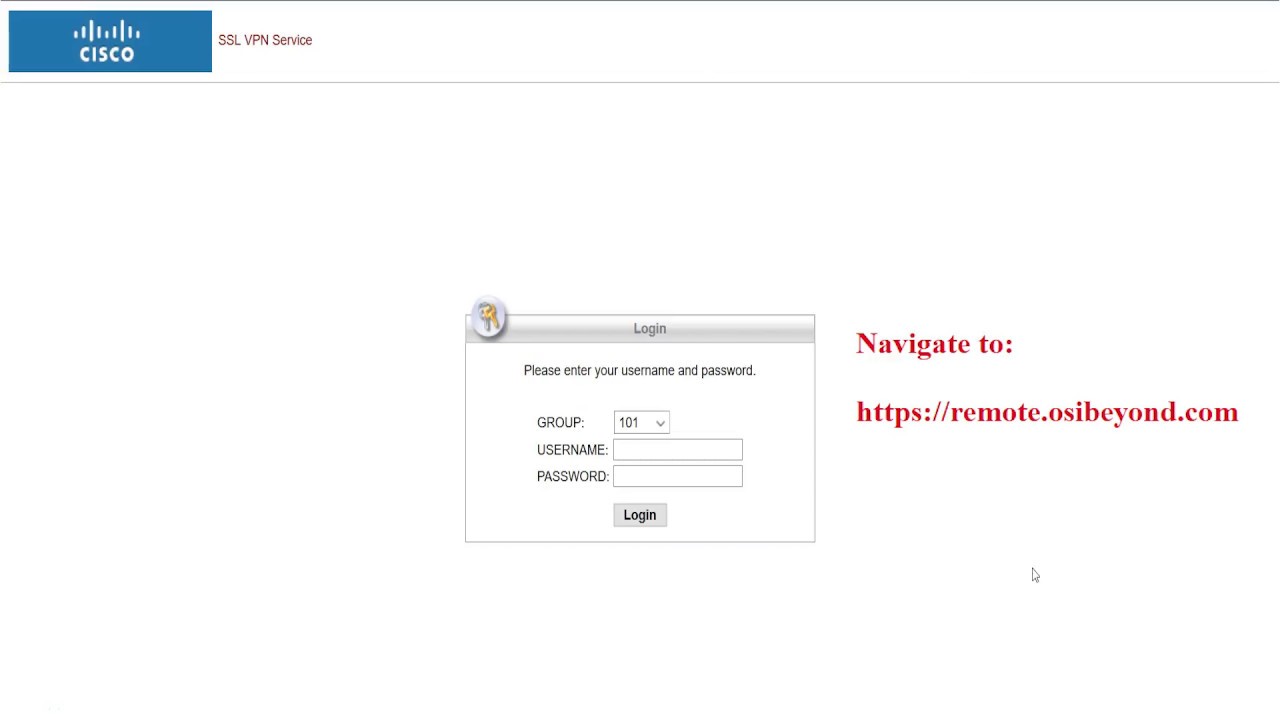
After you have installed the VPN Certificate on your system you can open up your web browser and navigate to https://vpn1.adams.edu
- Login with your ASU Domain Username and Password
- Click on 'AnyConnect'
- Click on 'Start AnyConnect'
- Click on 'Download for XYZ' the 'XYZ' will be replaced by either Windows / MAC or Linux depending from what system you are logging in from.
- Appendix
Refer to the steps below on how to configure Cisco AnyConnect VPN with CLI
Download Cisco AnyConnect 4.8 WebDeploy Client (anyconnect-win-4.8.02042-webdeploy-k9.pkg) from Cisco.com and upload to TFTP Server
Donwload Cisco AnyConnect Client to ASAv
- Verify the Anyconnect Package is downloaded to flash successfully
Preparation of required components
The following components will be need to be configured
- IP Pool (pool_ANYCONNECT) to assign IP address to AnyConnect Client
- Network object (obj_ANYCONNECT-POOL) for AnyConnect IP Pool
- Network object (obj_LAN) for Local LAN
- Access List for Split Tunnel (acl_SPLIT-TUNNEL)
Split tunneling to allow users to send only traffics to corporate network across the tunnel while all other traffics to Internet via the Local LAN
Group Policy (gp_ANYCONNECT) is a set of user-oriented attribute/value pairs for IPSec connections that are stored either internally (locally) on the device or externally on a RADIUS server
Connection Profile (prof_ANYCONNECT) uses a group policy that sets terms for user connections after the tunnel is established.
Multiple Connection Profiles can be defined and associate with different Group Policy
IP Pool for AnyConnect Client
Create an IP Pool for AnyConnect Client
Create a network object for AnyConnect IP Pool
Enable Cisco AnyConnect VPN with CLI on outside interface
Local User for AnyConnect VPN
Create a LOCAL username & password
Refer to Restrict Cisco AnyConnect VPN Login based on AD Group if you would like to integrate with Active Directory (AD) for Single Sign On (SSO)
Split Tunnel
Allow only traffic to corporate network via SSL VPN Tunnel
Group Policy
Create a new Group Policy – gp_ANYCONNECT to configure the internal DNS Server, Default-Domain, split-tunnel
Connection Profile
reate a new Connection Profile – prof_ANYCONNECT
Group-Alias to set the name which appear on the client login page below
No NAT for AnyConnect Client
Exclude traffic for AnyConnect Client (obj_ANYCONNECT-POOL) from being NATed
Save and Activate settings
Connect from Client Machine
Login to https://ASA_EXTERNAL_IP with the local username & password
Download and install Cisco VPN Client
Enter the Gateway IP / FQDN and click Connect
Perform the test below to verify the SSL VPN is working fine
- Ping to FQDN & IP Address of Internal Servers successfully
- Can Access to Internet as normal via existing Gateway
Refer to Let’s Encrypt SSL Certificate for Cisco AnyConnect VPN to replace the default selfsign SSL Cert with Public SSL Certificate to avoid the Certificate Error
Cisco Anyconnect Vpn Client Free Download For Mac Os X 10.8
Appendix
A. Stop the local user (vpn) from login to ADSM and CLI
Local User (VPN) created can be used to login to ASDM & SSH and we need to remove this for security concern
Enable Authentication & Authorization for http console
Assign Remote-Access attribute for normal user only
Access Lists for VPN Client
Access Lists can be configured to restrict AnyConnect VPN Client to have access to identified Services & Servers as below
Create a new Service Object (obj_TCP3389)for TCP 3389 (RDP)
Create a new Service Group (obj_SERVICES-VPN-IN) to allow only RDP & PING for AnyConnect VPN Client
Cisco Anyconnect Vpn Client 10.8 Free
Create an Access Rule – acl_OUT_ACCESS_IN and bind it to outside interface
Bind the Access List to Group Policy gp_ANYCONNECT
Cisco Anyconnect Vpn Client 10.8 Login
AnyConnect VPN Client connected to corporate network can only access
Cisco Anyconnect Vpn Client 10.8 Download
- Ping
- Remote Desktop (RDP)
- All other traffics will be blocked